Managing a Cyber-Crisis Incident: Six Operational Realities
Roger Mason PhD
Introduction
 Recently, I helped design my first cyber tabletop. My design partners handled the technical aspects while I focused on the overall design. The exercise participants were divided into four groups. Three groups were assigned a technical problem simulating a potential data breach. The fourth group was assigned the task of managing the collateral issues common to this type of incident. The exercise began and the problem solving commenced.
Recently, I helped design my first cyber tabletop. My design partners handled the technical aspects while I focused on the overall design. The exercise participants were divided into four groups. Three groups were assigned a technical problem simulating a potential data breach. The fourth group was assigned the task of managing the collateral issues common to this type of incident. The exercise began and the problem solving commenced.
I walked from group to group carefully listening to their comments and monitoring their results. The participants were operational managers from the corporation’s world-wide IT security team. The exercise players were highly experienced cyber problem solvers. The teams began working on their problems. The company response plans were provided to each participant to ensure their success.
 They immediately focused on the technical aspects of the problem and ignored the protocols in the response plan. I watched them at work. Their problem solving seemed to be influenced by three factors. First, this is “my comfort zone.” These individuals were promoted in part due to their technical knowledge and experience. Focusing on the technical solution was comfortable.
They immediately focused on the technical aspects of the problem and ignored the protocols in the response plan. I watched them at work. Their problem solving seemed to be influenced by three factors. First, this is “my comfort zone.” These individuals were promoted in part due to their technical knowledge and experience. Focusing on the technical solution was comfortable.
The second problem was the lure of a quick solution. Some of the participants were like a gambler trying to win back their losses. They knew they were expected to solve the problems employing their company protocols. The problem was they were unfamiliar with these plans. Their solution was gambling on a quick technical fix that would invalidate the need to follow any protocols. “If we can solve the problem why do we need to worry about the crisis management stuff?”
The third factor was the issue of teamwork. This could partly be excused by the fact these participants were not direct co-workers. Team members from around the world may have met for the first time just before the exercise. Once again the level of technical expertise proved to be an obstacle. There were a dozen experts on each team. Each person was convinced they had the answer.
I spoke to participants after the exercise. Some congratulated themselves on breezing through technical issues. Other participants were a bit more circumspect. They recognized as operational managers there might be a deeper level of problem solving. They were very clear on technical responses to a cyber incident but were unfamiliar with the greater issues of crisis management. I believe there are six realities that must be understood to improve operational management during a cyber-crisis.
Understanding the Battlespace
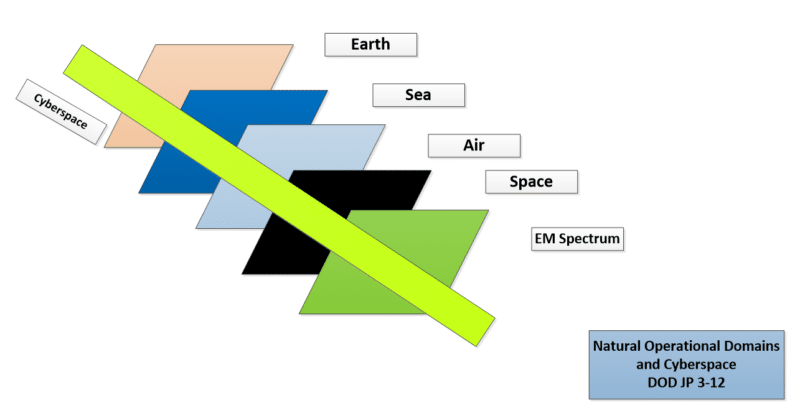
The first step in any conflict is understanding where the fighting will occur. The Department of Defense (DOD) calls this “the Battlespace.” .DOD Joint Publication 3-12, Cyber Operations provides a useful explanation of the natural domains involved in cyber operations.
The DOD identifies five natural operational domains where cyber operations can occur. Earth, sea, air, space, and the electromagnetic spectrum. Cyber operations can cut through each of the planes individually or all five domains simultaneously.
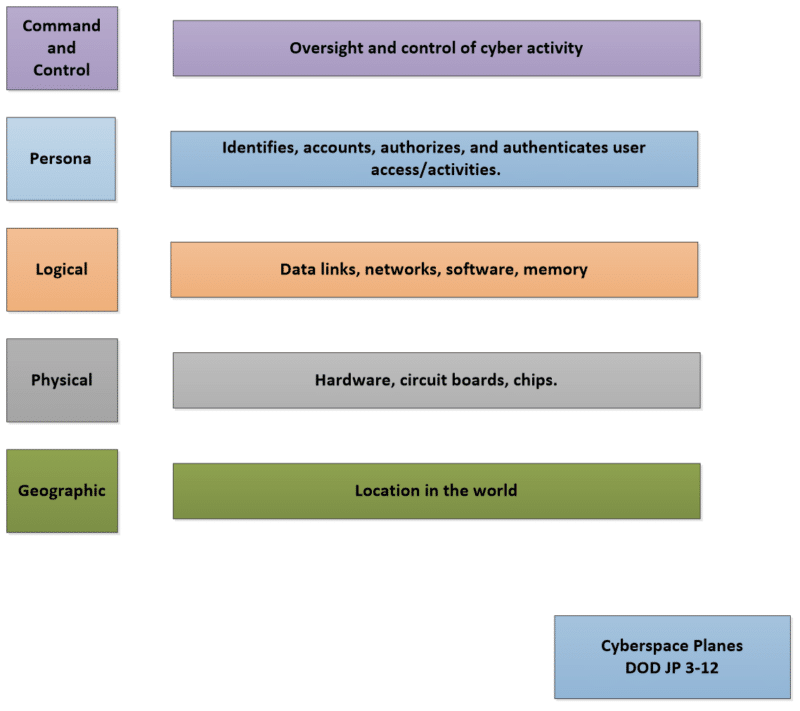
The DOD also recognizes five operational planes: command and control, persona, logical, physical, and geographic.
As an operational manager, you will be concerned with command and control. Your job is to oversee cyber activity. You will be managing the responders dealing with the Persona, Logical, and Physical domains. The Geographic plane involves your physical locations on the earth. If you are part of a worldwide organization the issue of time must be considered. Your operational response must take into account the local time of the responders. While the first four cyber planes are not time sensitive the personnel located in another part of the world will be.
Redirecting Your Focus
During our tabletop exercise the incident management team was presented with a series of problems. They immediately focused on a controversial issue that captured the team’s attention. The team become embroiled in a fruitless debate about the distressing topic.
As facilitator I finally asked if this problem was within their abilities to effectively address and resolve. They admitted it was not. We agreed it was better to use our limited problem solving resources on things that could be solved instead of fixating on something beyond our capabilities.
One of the hardest lessons in public safety critical incident management is you “can’t save every house.” Just like a brush fire that is moving too quickly to be stopped, every problem can’t be solved simultaneously. Effective cyber crisis managers understand that their response is limited to the extent of their incident intelligence and response resources.
Some problems may take days/weeks to identify and be so widespread that only portions of the problem can be addresses at any point in time. The goal is to effectively manage your intelligence and resources to intervene in the crisis and begin to control it.
Emphasizing Communications
During a cyber-crisis effective communications are important. The operational manager is responsible for communications. Communications is vertical and lateral. Vertical communications should go upward to executive decision makers above you and downward throughout the organization to persons and groups who may be impacted by the cyber incident. Lateral communications occur with the cyber responders within your response team.
You need to develop a communications plan. This is how and when you will communicate within your organization. Organizational chaos is encouraged when people have no idea what is happening. In the absence of regular communications people will assume nothing is happening. They will begin to self-communicate looking for information about what is happening.
The problem is particularly acute when the primary communications systems begin to fail. When people lose their communications platforms, they are encouraged to improvise “workarounds.” With the company email system compromised people will flood your cell phone with calls requesting information about what is happening. This can become a distraction to crisis management as your phone lights up with calls. The lack of communications also encourages uncoordinated attempts at local solutions that may inhibit more effective systemic problem solving.
(Note: To better understand the phenomenon of communications failures during crisis there are several excellent studies regarding the communications failure at Ground Zero on 9/11. The NYPD/NYFD had become more and more reliant on cellular communications. When it failed the command and control of the incident immediately degraded.
Radio communication systems became overwhelmed. Public safety responders could not communicate so they did not get the messages to respond to staging areas and not to the plaza between the twin towers. This resulted in a giant gridlock of police/fire personnel and equipment who were lost when the towers fell.
Why You Need Infrastructure
Persons who have made their career as solo problem solvers often do not understand the need for critical infrastructure during a cyber-crisis event. The more widespread the incident the greater need for infrastructure. Infrastructure is both physical and conceptual. Physical infrastructure is things like an emergency operations center and hardline phones. Conceptual in the infrastructure includes developing emergency operations plans and procedures.
In the 1970s Hewlett Packard was famous for an executive management approach they called MBWA (managing by wandering around). This technique emphasizes randomly wandering through work areas to get a more realistic sense of what is happening. This style of management has real value during normal operations Unfortunately many crisis managers brought up on wireless communications assume the best way to manage a crisis is to wander around. They also assume the wireless system they are relying on will always work.
If you are out wandering around when communications fails, your command and control of the incident is seriously degraded. I recommend that larger organizations have a dedicated emergency operations center. This is where information is collected and disseminated, planning is accomplished, and decisions are made. You should have wireless communications with a hardline backup. (This is especially important in an IT failure caused by a natural disaster.)
Conceptual infrastructure involves the emergency plans and procedures for your organization. The plan may require updates or improvements but everyone needs to be familiar with the plan. Without conceptual infrastructure all crisis response becomes a series of improvised work arounds. The challenge of relying on improvisation is the results may vary.
Preparing for a Crisis
The first step is training. Every person on the team must understand your plans and procedures. These plans and procedures must include a concept of operations (how you will respond) and understanding requirements like the DFARS responding/reporting protocols for US defense contractors. The second step is getting your infrastructure ready. The third step is tabletop exercises and wargames. Tabletop exercises are less formal and not as specific as a wargame. Tabletop exercise can be used to prepare your team. Wargames are designed to evaluate a specific problem or issue.
Summary
Effective crisis managers must bring a balance to their operations. They must overcome their naturally tendency to get directly involved in solving the problems. This requires understanding how to widen your focus. Operational managers must understand their battlespace and manage accordingly. An important part of the management process is understanding your limitations and communicating effectively. They will need infrastructure to support their operations. Mangers should employ exercises and wargaming to train and hone perishable operational skills.
None of these things are easy. The time to prepare is now and not when the first phone call alerts you to a problem. I recently spoke to a cyber manager about the use of exercises and wargames. He said, “I never do well in those things. But I know exactly what to do when a real cyber incident occurs.“ I hope he is right.